Quantum Cryptography Analogy Demonstration Kit

- Designed for Education, Demonstration, and Classroom Use
- Easy-to-Use Kits Include Components Plus Free Educational Materials

Please Wait

Click to Enlarge
Binary information encoded in the polarization state of light is detected by a sensor module (indicated by a blue LED).
Quantum Cryptography Analogy Demonstration Kit
- Designed for Educational, Demonstration, and Classroom Use
- Complete Photonics Kit Includes All Hardware Plus Extensive Manual and Teaching Materials
- Easy to Assemble and Use
- Choose from Educational Kits Containing Imperial or Metric Components
Experiment
- Learn How Information Can Be Encrypted and Sent Using the Polarization of Light
- Generate an Encryption Key that Allows for Private Communication
- Encrypt, Transmit, and Decrypt a Secret Message
- Examine How an Eavesdropper Causes Errors in Transmission that Can Be Detected
- Demonstrate the Steps of the BB84 Encryption Protocol
The EDU-QCRY1(/M) Quantum Cryptography Analogy Demonstration Kit contains components to model a data transmission setup using the BB84 encryption protocol. This encryption method allows a sender and receiver to generate an encryption key that only they know and eavesdroppers to be detected. In this analogy experiment, the polarization of transmitted light carries bits of information which are manipulated using half-wave plates and polarizing beamsplitters. The educational lab kit includes the lasers, half-wave plates, polarizing beamsplitters, and detectors required to model the sender (Alice), the receiver (Bob) and the eavesdropper (Eve).
Please note that this is a classical experiment that simulates the key principles used in quantum cryptography. As an analogy to the quantum setup, this experiment works with a pulsed laser instead of single photons. Single photon detectors are not included in this kit.
Thorlabs Educational Products
Thorlabs' line of educational products aims to promote physics, optics, and photonics by covering many classic experiments, as well as emerging fields of research. Each educational kit includes all the necessary components and a manual that contains both detailed setup instructions and extensive teaching materials. These lab kits are being offered at the price of the included components, with the educational materials offered for free. Technical support from our educational team is available both before and after purchase.
Purchasing Note: English and German language manuals/teaching information are available for this product. The imperial educational kit contains the English manual and US-style power cords. The appropriate manual and power cords will be included in the metric kit based on your shipping location. The power supplies and other electronic devices in both the metric and the imperial kit accept voltages of 230 VAC and 120 VAC. Please contact Tech Support if you need a different language, cord style, or power supply. As with all products on our website, taxes are not included in the price shown below.
This kit is designed to demonstrate the fundamentals of quantum cryptography and the BB84 encryption protocol through a series of classroom experiments. In these experiments, students will learn how to encode messages in binary using the polarization state of light and then encrypt them using the BB84 protocol.
The BB84 Protocol
The BB84 protocol is a communication scheme that combines an encryption technique known as the one-time pad with a quantum key distribution method. Message encryption using the one-time pad method is accomplished by adding a binary encryption key (consisting of 0s and 1s) to a message represented in binary. Because there is no methodology or pattern to the key or message, this method of encryption ensures that the encrypted message can be transmitted through public channels.
However, the fundamental challenge is ensuring that only Alice and Bob have knowledge of the encryption key and preventing an eavesdropper (designated as Eve) from intercepting the encryption key. The BB84 encryption protocol uses the idea of quantum key distribution (QKD) to ensure that only Alice and Bob have knowledge of the encryption key. QKD employs principles of quantum physics, such as the encoding of a single bit of information within a photon of light, to ensure that the information cannot be copied. Any interception attempt by Eve will inevitably change the state of the photon. Thus, the BB84 protocol offers the ability to send truly secure encrypted transmissions.
Modeling the BB84 Protocol Using the Polarization of Light
The EDU-QCRY1(/M) kit models the BB84 method using the polarization states of light (as illustrated in the diagram below). Data in the form of a bit is encoded into a pulsed laser beam by altering the polarization state. More specifically, the bit is encoded using a basis polarization pair (represented as a + or x) which converts the bit into a specific polarization angle. The + basis is represented by 0° and 90° polarizations while the x basis is represented by -45° and 45° polarizations. One of the polarizations in each pair represents a "0" bit while the other represents a "1" bit. Alice performs a transmission by emitting a pulsed beam of light and setting the polarization state with a half-wave plate to encode the bit and basis. The receiver (Bob) is equipped with a half-wave plate and beamsplitter to interpret the transmission as either a "0" or "1". The bits and bases are randomly chosen in each transmission; however by comparing bases, Alice and Bob can generate a unique encryption key only known to each other.
In this experiment, the eavesdropper (Eve) is represented by a module that can receive a transmission from Alice and then attempt to send the same signal to Bob. While Eve is free to do this since the "transmission" is public, students will learn how this will cause errors that reveal the presence of an eavesdropper. Because detection of an eavesdropper occurs during transmission of the encryption key, once Alice and Bob have verified that there is no eavesdropper, the message can be sent without risk of interception.
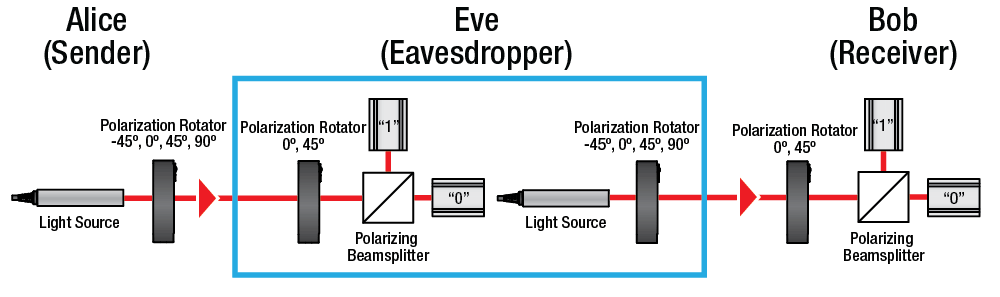
This schematic illustrates the Alice, Eve, and Bob modules of the EDU-QCRY1(/M) Quantum Cryptography Kit. The polarization state of light is changed by the polarization rotators to encode a "1" or "0" in a specific basis for transmission. The light is received by another polarization rotator, which allows the beamsplitter to send the light to the appropriate sensor for detection.
Single Photons Versus Classical Light
Genuine safety from an eavesdropper is only guaranteed if the BB84 protocol is carried out using single photons, which obey the “no cloning theorem”. In general, this theorem states a perfect copy of an unknown quantum state cannot be made without altering the state. As a result, Eve cannot copy a photon from Alice without altering it and cannot send an unaltered photon to Bob while keeping a copy for analysis.
Please note that the EDU-QCRY1(/M) analogy kit uses a pulsed laser source, i.e. classical light. While the sequence of the protocol is completely identical to the true quantum encryption system, it cannot be used as a perfect encryption system. Eve is able to eavesdrop unnoticed by separating a portion of the transmitted light for analysis while the remainder is sent to Bob.
This tab illustrates an example exercise that can be done by students using the EDU-QCRY1(/M) Quantum Cryptography Analogy Demonstration Kit. For full details on exercises and worksheets for students, please refer to the manual.
| Basis | Bit | Polarization |
|---|---|---|
| + | 0 | 0° |
| 1 | 90° | |
| × | 0 | -45° |
| 1 | 45° |
This example illustrates the generation of an encryption key between Alice and Bob, and the transmission a 10-bit, two-letter encrypted message using the BB84 protocol.
Generating an Encryption Key
First, Alice will randomly choose a sequence of bits and a basis (either + or ×) for the key transmission. The combination of bit and basis determines the polarization of the pulse of light transmitted by Alice (see the table to the right for possible combinations). Table 1 shows a sequence of 18 randomly chosen bits and bases, and the corresponding polarization angle. For further details on how to determine the polarization angle, please refer to the manual.
| Table 1: Transmitting (Alice) | ||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Index | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 | 13 | 14 | 15 | 16 | 17 | 18 |
| Alice's Basis (Random) | × | × | + | × | + | + | + | × | × | + | × | × | × | + | + | × | + | × |
| Alice's Bit (Random) | 1 | 0 | 0 | 1 | 1 | 0 | 0 | 1 | 1 | 1 | 0 | 1 | 0 | 0 | 0 | 1 | 0 | 1 |
| Polarization Angle | 45° | -45° | 0° | 45° | 90° | 0° | 0° | 45° | 45° | 90° | -45° | 45° | -45° | 0° | 0° | 45° | 0° | 45° |
At the same time, Bob chooses a random set of bases to use in receiving the transmission. These bases are chosen independently from Alice and will not always match. After transmission, Alice and Bob compare bases that they used. In cases where the basis matches with the one chosen by Alice (highlighted in green in Table 2), Bob will obtain the same bit as chosen by Alice. However, if the basis does not match, Bob will randomly receive a 0 or 1. Because the result is random, these bits are thrown out; the remaining green-highlighted bits become the encryption key between Alice and Bob.
| Table 2: Receiving (Bob) | ||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Index | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 | 13 | 14 | 15 | 16 | 17 | 18 |
| Bob's Basis (Random) | + | × | × | × | + | + | + | × | + | × | × | + | + | × | + | + | + | × |
| Bob's Bit (From Alice) | 1 | 0 | 1 | 1 | 1 | 0 | 0 | 1 | 1 | 1 | 0 | 1 | 0 | 1 | 0 | 0 | 0 | 1 |
In this example, the encryption key would be the sequence: "0 1 1 0 0 1 0 0 0 1".
Sending an Encrypted Message Using an Encryption Key
Now we will illustrate how to send a two-letter message "QM" using the encryption key above. First, each letter is converted into a 5-bit binary representation, as shown in Table 3 (see Chapter 9 of the manual for a reference table with binary representations for the full alphabet). While this example uses binary format to send alphabetical letters, any kind of information could theoretically be encoded into a binary sequence.
To encrypt the message, Alice performs binary addition on the message and encryption key (see the table below for addition rules). The resulting 10-bit message can then sent from Alice to Bob through public channels and using a previously agreed upon basis (i.e., Alice and Bob both choose to use either a + or × basis). After transmission, Bob can then decode the message by using binary addition on the encrypted message key using the encryption key. Because the results of binary addition are reversible, adding in this fashion returns the original binary message.
| Table 3: Sending an Encrypted Message | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| Lettera | Q | M | ||||||||
| Binary Message | 1 | 0 | 0 | 0 | 0 | 0 | 1 | 1 | 0 | 0 |
| Encryption Key | 0 | 1 | 1 | 0 | 0 | 1 | 0 | 0 | 0 | 1 |
| Encrypted Messageb | 1 | 1 | 1 | 0 | 0 | 1 | 1 | 1 | 0 | 1 |
| Binary Addition Rules |
|---|
| 0 + 0 = 0 |
| 0 + 1 = 1 |
| 1 + 0 = 1 |
| 1 + 1 = 0 |
This method for sending secure messages, however, assumes that no eavesdropper has knowledge of the encryption key. Because the transmissions described above are carried out via public channels, Eve can try to intercept the encryption key by intercepting the transmission between Alice and Bob. However, doing so will cause errors in the transmission. In the BB84 protocol, after comparing bases (Table 2), Alice and Bob will compare a test region of the encryption key. The errors introduced by Eve can be found by Alice and Bob when comparing the test region, alerting them to the presence of the eavesdropper. For a more detailed example, see Section 6.2 of the manual.
Quantum Cryptography Analogy Demonstration Kit Components

Thorlabs' Quantum Cryptography Analogy Demonstration Kit is available in imperial and metric versions. In cases where the metric and imperial kits contain parts with different item numbers, metric part numbers are listed next to their imperial counterpart and measurements are indicated in parenthesis.
| Kit Components | |||
|---|---|---|---|
| EDU-QCRY1 Item # |
EDU-QCRY1/M Item # |
Description | Qty. |
| MB8 | MB2020/M | Aluminum Breadboard 8" x 8" (20 cm x 20 cm) |
1 |
| MB810 | MB2025/M | Aluminum Breadboard 8" x 10" (20 cm x 25 cm) |
1 |
| MB1218 | MB3045/M | Aluminum Breadboard 12" x 18" (30 cm x 45 cm) |
1 |
| BA1 | BA1/M | Post Holder Base | 10 |
| PH2 | PH50/M | Post Holder, 2" (50 mm) Long | 5 |
| PH1.5 | PH40/M | Post Holder, 1.5" (40 mm) Long | 6 |
| UPH2 | UPH50/M | Universal Post Holder, 2" (50 mm) Long | 2 |
| TR1.5 | - | Optical Post, 1.5" Long | 6 |
| - | TR30/M | Optical Post, 30 mm Long | 4 |
| - | TR40/M | Optical Post, 40 mm Long | 2 |
| TR2 | TR50/M | Optical Post, 2" (50 mm) Long | 7 |
| RSP1X225-ALICEa | RSP1X225/M-ALICEa | Ø1" Indexing Rotation Mount, 22.5° Steps | 2 |
| RSP1X225-BOBa | RSP1X225/M-BOBa | Ø1" Indexing Rotation Mount, 22.5° Steps | 2 |
| PM3 | PM3/M | Clamping Arm | 2 |
| BA1S | BA1S/M | Swivel Post Holder Base | 1 |
| Kit Components | |||
|---|---|---|---|
| EDU-QCRY1 Item # | EDU-QCRY1/M Item # | Description | Qty. |
| AT1 | AT1/M | Alignment Tool | 1 |
| CL3 | CL3/M | Compact Variable Height Clamp | 2 |
| N/A | N/A | Kinematic Platform Mounta | 2 |
| RDF1 | Rubber Damping Feet (4 Pack) | 3 | |
| WPH10E-633 | Zero-Order Half-Wave Plate | 4 | |
| KM100 | Ø1" Kinematic Mount | 2 | |
| PBS201 | Polarizing Beamsplitter Cube | 2 | |
| AD11NT | Ø1" Adapter for Ø11 mm Components | 2 | |
| CPS635R-C2b | 635 nm Laser Diode Module | 2 | |
| BBH1 | Breadboard Handles | 1 | |
| SPW606 | SM1 (1.034"-40) Spanner Wrench | 1 | |
| N/A | Sensor Module | 4 | |
| N/A | Sensor Electronics Module | 2 | |
| N/A | Laser Electronics Module | 2 | |
| N/A | 5 V Power Supply | 4 | |
Imperial Kit: Included Hardware and Screws
| Item # | Description | Qty. | Item # | Description | Qty. |
|---|---|---|---|---|---|
| BD-3/16L | 3/16" Balldriver | 1 | - | 1/16" Hex Key | 1 |
| - | 9/64" Hex Key | 1 | - | 5/64" Hex Key | 1 |
| W25S050 | 1/4" Washer | 19 | SH25S038 | 1/4"-20 Cap Screw, 3/8" Long |
11 |
| SH25S050 | 1/4"-20 Cap Screw, 1/2" Long |
12 | SH25S063 | 1/4"-20 Cap Screw, 5/8" Long |
17 |
| - | 1/4"-20 Cap Screw, 1.25" Long |
2 | SH25S200 | 1/4"-20 Cap Screw, 2" Long |
2 |
| AS4M8E | M4 to 8-32 Thread Adapter | 4 | - | - | - |
Metric Kit: Included Hardware and Screws
| Item # | Description | Qty. | Item # | Description | Qty. |
|---|---|---|---|---|---|
| BD-5ML | 6 mm Balldriver | 1 | - | 1.5 mm Hex Key | 1 |
| - | 2 mm Hex Key | 1 | - | 3 mm Hex Key | 1 |
| W25S050 | M6 Washer | 19 | SH6MS10 | M6 Cap Screw, 10 mm Long |
11 |
| SH6MS12 | M6 Cap Screw, 12 mm Long |
12 | SH6MS16 | M6 Cap Screw, 16 mm Long |
17 |
| - | M6 Cap Screw, 30 mm Long |
2 | - | M6 Cap Screw, 45 mm Long |
2 |
User-Generated Content
Thorlabs' Educational Kits allow users to adapt the content to their own teaching needs. With that in mind, we enjoy hearing feedback from our customers with details about how they use the kits in their own classrooms. Use the Contact Us button to the right if you would like to submit your own user-generated content.
Second Wavelength and Decoy States
We cordially thank Brit Riggs and Professor Bertrand Cambou, Northern Arizona University, for sharing their following modification of the EDU-QCRY1 kit to demonstrate the use of a second wavelength and decoy states as an improvement upon the BB84 protocol.

User-Modified EDU-QCRY1 Kit
*Image courtesy of Brit Riggs and Professor Bertrand Cambou of Northern Arizona University.
Theory
BB84 is a well-known quantum key distribution (QKD) protocol that allows two parties to securely generate matching cryptographic keys by encoding information in single-photon polarization states. As an extension of the BB84 protocol, a second single-photon source with different wavelength may be introduced which doubles the number of usable polarization states. The largest advantage of a two-wavelength system over a single-wavelength system is that the two parties (Alice and Bob) no longer need to sacrifice a portion of their key to check for the presence of eavesdroppers (Eve). A subset of the additional polarization states can be used as "decoy states". These states are intentionally unused by Alice, but may be generated by Eve when intercepting Alice's transmission. If a statistically significant number of decoy states are detected by Bob, then he knows an eavesdropper must be present. For more information on decoy states and two-wavelength encoding, please see the synopsis here.
Like our standard EDU-QCRY1(/M), this custom quantum cryptography teaching kit uses pulsed lasers in order to emulate the behavior of a true quantum system. Therefore, while it is not a quantum safe communication setup, it is still ideally suited to teach students about quantum cryptography.
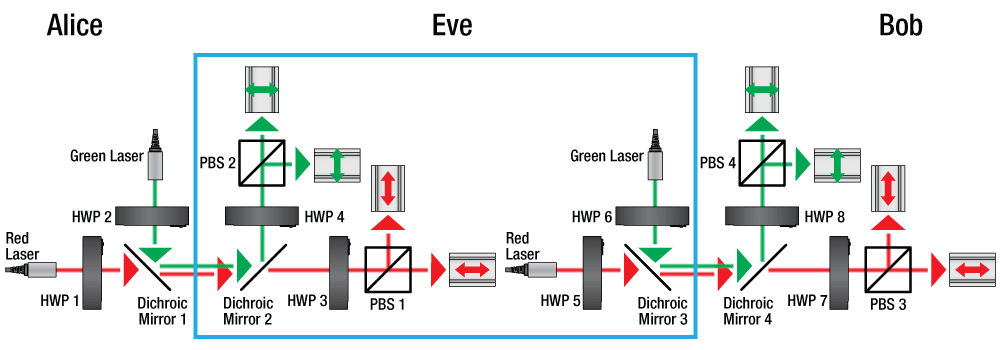
This schematic illustrates the Alice, Eve, and Bob modules that have been modified to incorporate a second wavelength. There are four polarization states across two bases per wavelength which may be used to encode information. Dichroic mirrors are used to combine and separate the different wavelengths for transmission and measurement respectively. (HWP: Half-Wave Plate, PBS: Polarizing Beamsplitter)
Key Additional Components
The following partial list of components may be used to incorporate a second wavelength into the EDU-QCRY1(/M) kit:
- 2X CPS520 520 nm Laser Diode Module
- 2X Laser Electronics Module
- 4X Sensor Modules
- 2X Sensor Electronics Module
- 2X PBS201 20 mm Polarizing Beamsplitter Cube, 420 - 680 nm
- 4X WPH10E-514 Ø1" Polymer Zero-Order Half-Wave Plate, 514 nm
- 4X DMLP605 Ø1" Longpass Dichroic Mirror, 605 nm Cut-On
For a complete list of components, please contact Tech Support.
The EDU-QCRY1(/M) was developed in cooperation with several educators and organizations specializing in teaching quantum physics:
- Jörn Schneider, Leibniz-Gymnasium Dormagen
- Jan-Peter Meyn and Andreas Vetter, University Erlangen-Nuremberg (www.quantumlab.de)
- Quantum Physics in School 2014 Meeting, Munich (www.heisenberg-gesellschaft.de)
Do you have ideas for an experiment that you would like to see implemented in an educational kit? Contact us at techsupport@thorlabs.com; we'd love to hear your ideas.
Laser Safety and Classification
Safe practices and proper usage of safety equipment should be taken into consideration when operating lasers. The eye is susceptible to injury, even from very low levels of laser light. Thorlabs offers a range of laser safety accessories that can be used to reduce the risk of accidents or injuries. Laser emission in the visible and near infrared spectral ranges has the greatest potential for retinal injury, as the cornea and lens are transparent to those wavelengths, and the lens can focus the laser energy onto the retina.
Safe Practices and Light Safety Accessories
- Laser safety eyewear must be worn whenever working with Class 3 or 4 lasers.
- Regardless of laser class, Thorlabs recommends the use of laser safety eyewear whenever working with laser beams with non-negligible powers, since metallic tools such as screwdrivers can accidentally redirect a beam.
- Laser goggles designed for specific wavelengths should be clearly available near laser setups to protect the wearer from unintentional laser reflections.
- Goggles are marked with the wavelength range over which protection is afforded and the minimum optical density within that range.
- Laser Safety Curtains and Laser Safety Fabric shield other parts of the lab from high energy lasers.
- Blackout Materials can prevent direct or reflected light from leaving the experimental setup area.
- Thorlabs' Enclosure Systems can be used to contain optical setups to isolate or minimize laser hazards.
- A fiber-pigtailed laser should always be turned off before connecting it to or disconnecting it from another fiber, especially when the laser is at power levels above 10 mW.
- All beams should be terminated at the edge of the table, and laboratory doors should be closed whenever a laser is in use.
- Do not place laser beams at eye level.
- Carry out experiments on an optical table such that all laser beams travel horizontally.
- Remove unnecessary reflective items such as reflective jewelry (e.g., rings, watches, etc.) while working near the beam path.
- Be aware that lenses and other optical devices may reflect a portion of the incident beam from the front or rear surface.
- Operate a laser at the minimum power necessary for any operation.
- If possible, reduce the output power of a laser during alignment procedures.
- Use beam shutters and filters to reduce the beam power.
- Post appropriate warning signs or labels near laser setups or rooms.
- Use a laser sign with a lightbox if operating Class 3R or 4 lasers (i.e., lasers requiring the use of a safety interlock).
- Do not use Laser Viewing Cards in place of a proper Beam Trap.
Laser Classification
Lasers are categorized into different classes according to their ability to cause eye and other damage. The International Electrotechnical Commission (IEC) is a global organization that prepares and publishes international standards for all electrical, electronic, and related technologies. The IEC document 60825-1 outlines the safety of laser products. A description of each class of laser is given below:
| Class | Description | Warning Label |
|---|---|---|
| 1 | This class of laser is safe under all conditions of normal use, including use with optical instruments for intrabeam viewing. Lasers in this class do not emit radiation at levels that may cause injury during normal operation, and therefore the maximum permissible exposure (MPE) cannot be exceeded. Class 1 lasers can also include enclosed, high-power lasers where exposure to the radiation is not possible without opening or shutting down the laser. |  |
| 1M | Class 1M lasers are safe except when used in conjunction with optical components such as telescopes and microscopes. Lasers belonging to this class emit large-diameter or divergent beams, and the MPE cannot normally be exceeded unless focusing or imaging optics are used to narrow the beam. However, if the beam is refocused, the hazard may be increased and the class may be changed accordingly. |  |
| 2 | Class 2 lasers, which are limited to 1 mW of visible continuous-wave radiation, are safe because the blink reflex will limit the exposure in the eye to 0.25 seconds. This category only applies to visible radiation (400 - 700 nm). |  |
| 2M | Because of the blink reflex, this class of laser is classified as safe as long as the beam is not viewed through optical instruments. This laser class also applies to larger-diameter or diverging laser beams. |  |
| 3R | Class 3R lasers produce visible and invisible light that is hazardous under direct and specular-reflection viewing conditions. Eye injuries may occur if you directly view the beam, especially when using optical instruments. Lasers in this class are considered safe as long as they are handled with restricted beam viewing. The MPE can be exceeded with this class of laser; however, this presents a low risk level to injury. Visible, continuous-wave lasers in this class are limited to 5 mW of output power. |  |
| 3B | Class 3B lasers are hazardous to the eye if exposed directly. Diffuse reflections are usually not harmful, but may be when using higher-power Class 3B lasers. Safe handling of devices in this class includes wearing protective eyewear where direct viewing of the laser beam may occur. Lasers of this class must be equipped with a key switch and a safety interlock; moreover, laser safety signs should be used, such that the laser cannot be used without the safety light turning on. Laser products with power output near the upper range of Class 3B may also cause skin burns. |  |
| 4 | This class of laser may cause damage to the skin, and also to the eye, even from the viewing of diffuse reflections. These hazards may also apply to indirect or non-specular reflections of the beam, even from apparently matte surfaces. Great care must be taken when handling these lasers. They also represent a fire risk, because they may ignite combustible material. Class 4 lasers must be equipped with a key switch and a safety interlock. |  |
| All class 2 lasers (and higher) must display, in addition to the corresponding sign above, this triangular warning sign. |  |
|
| Posted Comments: | |
Willem Rovers
(posted 2024-02-27 09:50:14.333) Best,
I can no longer turn on/pulse the laser with the laser electronics unit. The LED also does not light when I connect it to power. What can be the problem? hchow
(posted 2024-02-29 07:29:29.0) Dear Mr. Rovers, thank you for your feedback. I believe the problem might possibly lie in the laser electronics unit like you have mentioned. I will personally reach out to you to see how best we can solve this issue. Thank you. Josef Kölbl
(posted 2024-01-08 12:17:37.74) Hello,
we bought the thorlabs quantum cryptography analogy demo kit many years ago. And students use it almost every semester in a lab experiment.
Question: Could we actually purchase the sensor module and/or the sensor electronics module and/or the laser electronics module separately? Just in case to have spare parts? In the kit components list these parts appear as N/A.
Thanks, Josef. hchow
(posted 2024-01-08 09:48:23.0) Dear Mr. Kölbl, yes you can in fact purchase the individual components of the quantum cryptography kit if you wish to. You would just have to let us know exactly which components it is you want. Thank you. Vin Tan
(posted 2023-10-09 16:18:44.547) Hi, this is more of a query then feedback. I have bought the quantum cryptography educational kit earlier this year through your Singapore distributor.
I would like to find out, for the sensor module, as compared to single photon detector, how big are the differences? If i would like to simulate an attack on the photon detector conceptually, am i able to use the sensor module? fmortaheb
(posted 2023-10-09 05:16:06.0) Thank you very much for contacting us. I'll contact you directly to discuss your application in detail. Patrick Bales-Parks
(posted 2021-08-23 15:19:40.147) Hello, Our University is looking at ordering a few of these kits. I would like to know if the kits come in a storage case? soswald
(posted 2021-08-25 09:31:13.0) Dear Patrick,
thank you for your feedback. To move towards increased sustainability we have switched from plastic cases to cardboard packaging where possible. Therefore the EDU-QCRY1/M kit is shipped in cardboard boxes. Anitha Kumari K
(posted 2021-07-20 02:18:09.563) Dear Sir,
Myself Dr.Anitha from India!! To continue my research project, I would like to procure Quantum Cryptography Analogy Demonstration Kit!!
In this regard, I would like to know the Price of Quantum Cryptography Analogy Demonstration Kit and Local Vendor available in India to procure the device!!
Regards,
Dr. K. Anitha Kumari, ME., MBA., Ph.D.
ASSOCIATE PROFESSOR
Department of Information Technology
PSG College of Technology
Coimbatore - 641 004, TN, India.
Phone: +91 9842525820 soswald
(posted 2021-07-23 03:57:52.0) Dear Anitha,
thank you for your feedback.
The price of the EDU-QCRY1 kit is 3224.41 € + VAT and shipping.
You can find our list of distribution partners here:
https://www.thorlabs.de/distributors.cfm
For India this is MEL Systems and Services Ltd.
P: 91-44-24961903/904
F: 91-44-24960488
E: sales@melss.com mike antunes
(posted 2020-10-18 13:29:49.597) Could i get more information on this kit?
I not sure how to send a message.
thanks
mike nreusch
(posted 2020-10-21 04:29:33.0) Thank you for contacting us. In the BB84 protocol, Alice and Bob generate the key for the communication. With that key, the message is encrypted. To actually send the message, it is encoded in binary, meaning 0s and 1s. Then, a pulse with, e.g., 0° orientation is defined as “0” and 90° orientation is defined as “1”.
You can find a description of the experiments of this kit by clicking on the “Experiment” tab on top of the page. The manual for this kit is also free for download. Chapter 6 features detailed examples of the entire process from key generation over the transmission to the detection of an eavesdropper. If you have any further questions, please contact your local tech support team. cyasar
(posted 2018-02-14 13:31:00.61) Hello I am Cumali YAŞAR; I am a Ph.D. student at Çanakkale Onsekiz Mart University. I wrote a project on Quantum Key Distribution. The budget is low. We decided to buy "Quantum Cryptography Demonstration Kit" as a team.
We need some information from you guys.
Question -1: Do you send the technical specifications for the purchase?
Question 2: Can the Quantum Cryptography Demonstration Kit be controlled by a computer? How do we get the results of the squeeze process.
We thank you. jkuchenmeister
(posted 2018-02-14 10:07:57.0) This is a response from Jens at Thorlabs: Question 1: I'll get in touch with you via e-mail. Question 2: At the moment, the experiment does not feature a computer control. The laser pulses are released manually. The information which detector responds is given by the signal LEDs at the top of the sensor units.
Please note that there is no squeeze process. The kit is a purely classical demonstration kit with a pulsed laser. There is no actual quantum physics going on. However, since the polarization state of light is similar for a classical wave and single photons, students can go through the whole BB84 protocol (preparation of the state, measurement, etc.) to understand this protocol of quantum cryptography. |
 Products Home
Products Home




















 Quantum Cryptography Kit
Quantum Cryptography Kit